Quick overview:
Die Entwicklung zum XP-Nachfolger „Vista gelangt zum vorläufigen Stillstand: Group Vice President Jim Allchin setzte die Prioritäten der Entwicklerteams in den vergangenen Monaten nun endgültig auf XP-SP2 fest. Microsoft möchte sich mit dem Service Pack 2 tapfer aktuellen Viren, Sicherheitslücken und Hackern entgegenstellen. Trotz der Verschiebungen von Windows Server 2003 SP1, Vista und natürlich dem SP2 selbst bedeutet dies ein entscheidender Schritt im Sicherheits-Prestigeduell zwischen Windows und Linux. Bislang war und ist Windows XP noch nie sicherer gewesen: Das übersichtliche „Sicherheitscenter, die brandneue Firewall, der Pop-Up Blocker, die sinnvolle IE-Add-On Verwaltung und modernste Speicherschutz-Technologien stellen nur einen Teil dieses Sicherheits-Sprungbrettes dar.
Windows-Tweaks zeigt Ihnen in diesem Artikel, was Sie mit dem Service Pack 2 erwartet:

Data Execution Prevention (DEP) - protection against buffering
Die so genannte DEP-Technologie schützt Ihren Rechner indem sie das Ausführen von nicht zulässigen Dateien a la Viren oder Würmer verhindert. Mit Hilfe des Prozessors setzt sie einen Prozess auf Nicht-Ausführbar, wenn sich kein explizit ausührbarer Code dahinter verbirgt. Die meisten Viren bzw. andere Schädlingsprogramme kopieren sich in diese Speicherbereiche und starten sie von dort aus. Sollte dennoch versucht werden hier ausführbare Daten zu starten, springt prompt die CPU ein und verhindert durch das Setzen einer „Ausnahme im Speicher das Starten der jeweiligen (gefährlichen) Anwendung. AMD nennt diese eigene Technologie „No-execute (NX) – sie wird bei 64-Bit Prozessoren in verstärkter Form Einsatz finden, da hier wesentlich mehr Bereiche des Kernels im Vergleich zur reinen 32-Bit Umgebung geschützt werden
![]()
E-mail protection and new Internet Explorer techniques
Trotz der Behandlung als „schwarzes Microsoft-Schaf erfährt Outlook Express nun einige interessante Neuerungen auf dem langen Weg zu SP2. Es wandelt ab sofort HTML-Mails, deren unsichtbare E-Mail Köpfe (Header) gefährliche Scripte beinhalten können, automatisch in „Nur-Text-Nachrichten um und schützt den Benutzer der elektronischen Postkutsche vor heikler Datenspionage, Absturz oder Datenverlust. Starten Sie OE und testen Sie dieses digitale Raffinesse selbst: Unter „Extras/Optionen…/Lesen und „Senden finden Sie entsprechende „Nur-Text Optionen. Über „Ansicht/Nachricht in HTML betrachten Sie, bei sicherer Quelle, dann direkt die Original-Nachricht im Urformat (mit Bildern, Formatierungen etc.). Interessant ist auch der Schutz vor externem HTML-Code und Bildern, den Sie in den Optionen unter „Sicherheit vorfinden. Spam-Anbietern spucken Sie in die Suppe: Diese schicken Ihnen Mails mit Verweisen auf externe Daten.. Sobald Ihr Rechner diese Daten innerhalb einer Mail herunter lädt, erfolgt eine verhängnisvolle Verifizierung beim Spam-Server. Der berüchtigte Hersteller sendet Ihre Adresse, da sie existiert und Sie sie abfragen, an weitere Anbieter. Die Spam-Flut ist dann kaum noch aufhaltbar und beschert Ihnen in kürzester Zeit ein offenes Post-Scheunentor, das dubiose Werbetaktiker geschickt zur zweifelhafte Einnahmequelle nutzen. Das SP2 erstickt die Vermehrung von Spam-Mails und das lästige Einwählen zum Download externer Daten glücklicherweise rücksichtlos im Keim.
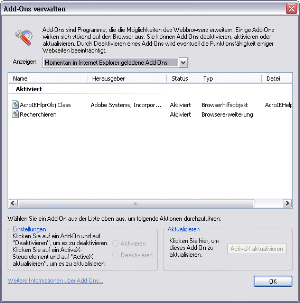
Der Internet Explorer wurde ebenfalls in vielerlei Bereichen deutlich aufgebohrt. Er verfügt nun über einen raffinierten„Publisher Check (Überprüfung des Herstellers), der eine Datei auf sicheren Ursprung verifiziert. Er zeigt bei kritischen und risikoreichen Dateien (.exe, .zip) Herstellerinformationen an, sobald diese herunter geladen oder als Anhang (OE) geöffnet werden. Programmen mit nicht zertifiziertem Code wird somit ein (zwar kleiner, dennoch störender) Stolperstein in den Weg gestellt – es bleibt nur eine Frage des berühmten Katz & Maus-Spiels, bis diese Zertifizierungen geknackt werden. Direkt hiermit verbunden ist die Webbrowser Add-on Verwaltung des Internet Explorers. Der Benutzer kann sich mit diesem kleinen Helferlein vor der Spyware-Bedrohung zumindest grundlegend retten: Klicken Sie im IE auf „Extras/Add-ons verwalten…. Dieses essentielle Werkzeug liefert dem Benutzer Backstage-Karten zum Internet Explorer Spyware-Treff. Bislang gelingt es jedem zweifelhaftem Stück Software sich unbemerkt ins System einzunisten, hier Unwesen zu treiben und versteckt das Dasein zu fristen. Die Internet Explorer „Absturz-Erkennung ist mit der Add-On-Verwaltung fest verschmolzen. Sie erkennt Abstürze, die von IE-Erweiterungen (meist entwickelt von Drittherstellern) her rühren und gibt dem Benutzer entsprechende Eiinblicke. Öffnen Sie die Add-On-Verwaltung, wie oben beschrieben, und betrachten Sie die Liste. Über das Auswahlmenü können Sie zwischen zurzeit verwendeten (also in jeder Instanziierung des IE geladenen) und allen installierten Erweiterungen (Add-ons) entscheiden; meist lässt sich die eine oder andere Einnistung entfernen. Spyware übermittelt nicht nur Statistiken Ihre Internet-Routine oder persönliche Daten an einen Server sondern spielt, dank schlechter Programmierung, auch eine große Rolle bei IE-Abstürzen oder „Seite nicht gefunden Browserfehlern. Sie können in der Verwaltung auf ein Objekt klicken und dies „Aktivieren oder „Deaktivieren, falls es Ihnen seltsam vorkommt. Sollten Sie nicht wissen, wofür ein Add-on steht, so hilft „www.google.de mit der entsprechenden Eingabe des Namens sicher weiter.
Achtung: Viele Software-Hersteller vertrauen auf den Internet Explorer als Basis Ihrer Anwendungen, weshalb Sie Vorsicht bei der Deaktivierung gewisser Komponenten walten lassen sollten.
![]()
Windows XP Media Center Edition and Tablet PC with SP2 ?
Benutzer der Erstausgabe der Windows Media Center Edition (Version 2003) schätzen sich glücklich, denn die Installation des Service Packs 2 beschert ihnen ein komplettes Upgrade auf die Vorzüge der MCE 2004. Eine verbesserte und stabilere Oberfläche, der neue Media Guide, Erkennung von Dritthersteller-Add-Ons oder die Unterstützung von Widescreen-Anzeigegeräten ist nur eine kleine Liste der interessanten Neuerungen. Auch Tablet PCs kommen in den Genuss der aktuellen Variante (Codename „Lonestar), die mit erheblich besserer Schrifterkennung den im Moment noch lahmenden Tablet PCs einen Verkaufsschub ermöglichen soll. Fazit: Besonders Benutzer der MCE-/TPC-Technologien profitieren von Microsofts XP-SP2.

Behind the scenes: The security center
Eine der „zentralsten Neuerungen, die mit dem Windows XP Service Pack 2 an Bord geschwemmt werden, ist das „Sicherheitscenter. In die Systemsteuerung nistet sich diese komfortable Überwachungssoftware ein und benutzt Microsofts WMI-Schnittstelle (Windows Management Instrumentation), die eine Erweiterung zum WDM, dem Windows Treibermodell, darstellt um den Status verschiedener Sicherheitsaspekte des Systems abzufragen. WMI bietet Anwendungen oder Treibern die Möglichkeit der direkten Integration und Interaktion mit Windows, so das Informationen und Benachrichtigungen herausgegeben werden können: In Zukunft werden sich viele Dritthersteller von Firewalls und Antiviren-Lösungen über WMI ins Sicherheitscenter einklinken. Laut Microsoft ist das Center dann z.B. in der Lage zu überprüfen, ob die aktuelle Virendefinition aktuell ist oder ob der Echtzeitvirenschutz aktiv im Hintergrund arbeitet.

Windows XP SP2 for pirates
„Wir erwarten, dass fast alle Windows XP Benutzer mit originalen oder illegalen Versionen den Zugriff auf die Sicherheitstechnologien des SP2 haben, ließ Gary Schare, Sicherheitsdirektor bei Microsoft, verlauten. Diese Meldung schlug positiv ein, da in der Vergangenheit hunderttausende Besitzer illegaler Kopien von den Vorteilen des Service Packs 2 ausgeschlossen werden sollten. Build 2180 (die finale Version des SP2) wird sich nach langem Microsoft-internen Hin und Her doch gegenüber Raubkopierer öffnen und soll verhindern, dass die Ausbreitung von Gefahrenherden wie z.B. Sasser oder myDoom über diese illegalen Versionen weiterhin erfolgt. Lediglich die Product Keys, die von Microsoft bereits für das Service Pack 1 verboten wurden, werden auch weiterhin geblockt. Raubkopierer haben allerdings schon neue Keys gefunden, mit denen das SP2 definitiv funktioniert.

Windows Update V5 - Increased focus on updates
Was früher bei vielen Benutzern als unbeliebtes Windows-Nebenprodukt abgetan wurde, könnte sich zur populärsten Funktion herauskristallisieren. Das Windows Update wird nicht mehr einfache (jedoch kritische) Updates für Windows installiert; V5 ist ab sofort auch in der Lage Prioritäten anhand zurzeit herrschender Bedrohungen zu setzen und diesen Patches den verdienten Vorrang zu erteilen – und das noch bevor unwichtigere Aktualisierungen den Weg ins System finden! Der brandneue BITS 2.0 (Background Intelligent Transfer Service) hat in Sachen Intelligenz nun um mehrere Spuren zugelegt. Er erledigt den (in Sachen Geschwindigkeit) dynamisch anpassbaren Download des Updates wesentlich schneller, da bei neueren Versionen einer bereits herunter geladenen Datei lediglich die aktualisierten Bytes übertragen werden.
Sie können sich über http://v5.windowsupdate.microsoft.com von der Qualität der brandneuen Windows Update V5 Seite überzeugen: Das SP2 steht hier im (anpassbaren) Download schon zur Verfügung und verkürzt die Wartezeiten, da im Schnitt lediglich 100 MB (abhängig von System) an geänderten Dateien übertragen wird.

The first contact: Service Pack 2 and the online world
Die „Internetverbindungsfirewall (ICF) wurde nun zur „Windows-Firewall umgetauft und bietet im Zuge dieser Namensänderung etliche neue Wege um TCP/IP (v4 und v6) Transaktionen, sprich der Kontakt zum Internet, sicherer zu gestalten. Die bzw. der (wie es in der Microsoft-Sprache korrekt heißen müsste) Firewall verhindert ein- und ausgehende Verbindungen, indem Ports einzeln gesperrt werden. Die Service Pack 2 Firewall bietet in der aktuellsten Version auch BootTime-Sicherheiten, die Ihren Rechner schon beim Hochfahren vor Würmern, Hackern oder anderen lauernden Gefahren effektiv schützen – bislang wurde der Firewall-Dienst erst in den letzten Phasen des Windows-Startprozesses aktiv, was Ihren PC für einen kurzen Zeitrahmen zum offenen Scheunentor machte.
Die neue Firewall bietet nun Kommandozeilen-Unterstützung über die sie sich dank „netsh per Befehl blitzschnell konfigurieren lässt – doch auch eine neue, einfache, Benutzeroberfläche blickt dem Windows-Benutzer in der „Systemsteuerung entgegen. Über diese Firewall-Verwaltung können Sie den essentiellen Onlineschutz (de)aktivieren, Ausnahmen für bestimmte Programme setzen oder entscheiden, für welche Verbindung Sie die Firewall nutzen. Die folgenden Tipps sind Ihr Schlüssel zur Firewall: Wir zeigen Ihnen Wege, wie auch mit aufgefahrenen SP2-Geschützen der Weg ins Internet nicht von überflüssigen Beschränkungen durchsetzt sind.
Wir hoffen, Ihnen einen grundlegenden Einblick in die Neuerungen von Service Pack 2 gegeben zu haben. Weitere Informationen erhalten Sie unter Frequently Asked Questions - Windows XP Service Pack 2 Frage & Antwort .
NOTE FOR NEW PUBLICATION: This article was produced by Sandro Villinger and comes from the Windows Tweaks archive, which has been built up since the late 1990s.
On Windows Tweaks you will find time-saving tech guides for PC, software & Microsoft. For a stress-free digital everyday life. Already we have been "tweaking" Windows since 1998 and just won't stop!



